Don’t Overlook the Weakest Link in Your Network: Strengthening Layer 2 Security with DrayTek
The Threat
Even with a robust firewall guarding your network's Internet edge, your LAN may still be exposed to internal threats.
While Layer 7 firewalls and deep packet inspection technologies are on the rise—often marketed with advanced features and high price tags—these tools primarily focus on the boundary between your LAN and the wider Internet. Despite their sophistication, they do little to secure what lies inside: your Layer 2 infrastructure.
Until recently, it was hard for SMBs to find effective Layer 2 protection that didn’t require enterprise-level budgets. DrayTek security routers are an exception—offering enterprise-grade features at SMB-friendly prices.
Your Greatest Security Risk May Be Within
Traditional firewalls—especially those designed for SMBs—can't stop Layer 2 attacks because they happen before traffic ever reaches the firewall. Internal LAN threats are often underestimated, yet they can be the most damaging. IT admins, MSPs, and integrators must recognize the growing risk from internal devices: IP phones, printers, cameras, and countless IoT gadgets—many of which are cheaply made, insecure, or even embedded with malicious code.
Recent news reports have highlighted hundreds of thousands of compromised cameras, printers, and routers running unauthorized software—all of them living on internal LANs, free to attack PCs and servers from within.
Rogue devices, duplicated IPs, ARP spoofing, network loops from misconnected cables—these attacks all operate at Layer 2 and completely bypass traditional firewall protections. A simple mistake, like plugging a switch into the wrong port, can grind a network to a halt. These issues are preventable, but only at the switch level.
It's alarmingly easy for someone to connect a rogue device to an open network port—on the wall, behind an IP phone, or in an undersecured closet. Even worse, they can configure that device with a duplicate IP address of a vital component—such as your router, PBX, DNS, or file server—causing traffic misrouting or total service disruption.
Infected devices already on your LAN can do the same damage without any visible intrusion. The resulting chaos—slow connections, dropped services, unresponsive apps—can take days for seasoned network pros to diagnose, often requiring hours of packet captures and MAC address analysis.
All of it happens at Layer 2. And all of it can be stopped—at the switch.
The Solution
Fortunately, these problems don’t require expensive enterprise gear to fix. With the right switch and a few smart configurations, you can defend your LAN effectively—without breaking your budget.
Although some Intrusion Detection Systems (IDS) offer mitigation options, few are truly SMB-friendly. Most are either overly complex or cost-prohibitive.
Some managed switches on the market do offer VLANs, ACLs, and loop prevention, but often lack the intelligence or simplicity to deal with modern LAN-based threats. What’s really needed is a new class of smart switches—ones that act as Layer 2 firewalls.
DrayTek's business switch lineup—including the VigorSwitch 1282, 2282x, 2100, and 2540 series—has been enhanced with Layer 2 security tools tailored for IT professionals, integrators, and MSPs. No licensing fees, no maintenance contracts—firmware updates are always free. These switches bring enterprise-level protections within reach.
Key Layer 2 Security Features from DrayTek
🔒 Simple Layer 2 Port Security
This feature lets you tightly control what types of Layer 2 hosts are allowed on each switch port. Configuration is simple, either through a GUI or setup wizard—no deep firewall expertise required.
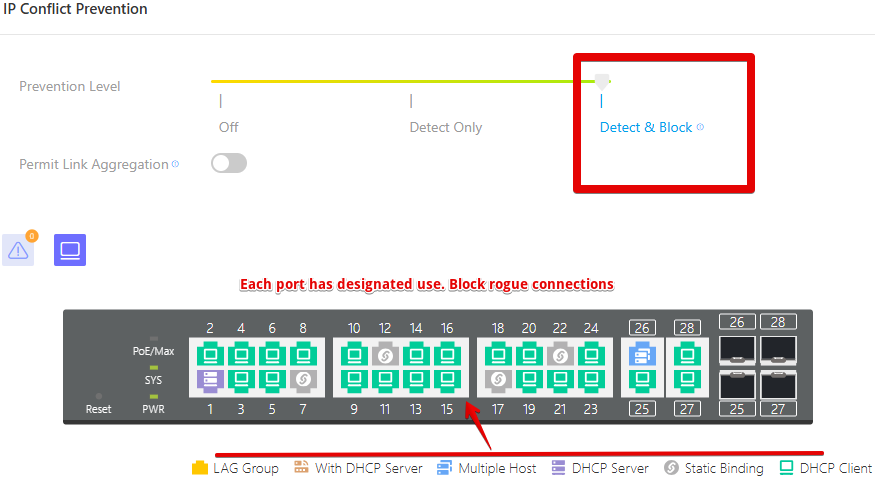
- DHCP or Static IP Control
Define whether a port accepts DHCP clients or only static IPs. Prevents rogue devices from connecting with unauthorized configurations.
- Single or Multiple Host Mode
Limit ports to a single device or permit multiple MACs. Prevents unauthorized switches or devices from branching off an approved connection.
- Static IP-Port Binding
Bind critical IP addresses (like servers) to specific ports. No other port will accept traffic from a device using that IP, eliminating IP conflicts and impersonation.
- DHCP Server Lockdown
Block unauthorized DHCP servers. Prevents misconfigured devices or malware from hijacking IP assignment and traffic flow.
🛡️ IP Source Guard/ACL
Lock down ports to accept only specific IP or IP-MAC combinations. If a different device tries to connect—even with the same IP—it will be denied. This stops rogue devices or spoofed clients at the entry point.
Example: Ports 24 and 25 are locked to a specific server. Any other device, even with matching IPs, is blocked.
🔥 Layer 2 Firewall for MAC, IPv4, and IPv6
This feature provides a more comprehensive security layer at the switch, enabling rule creation for MAC addresses and IPs.
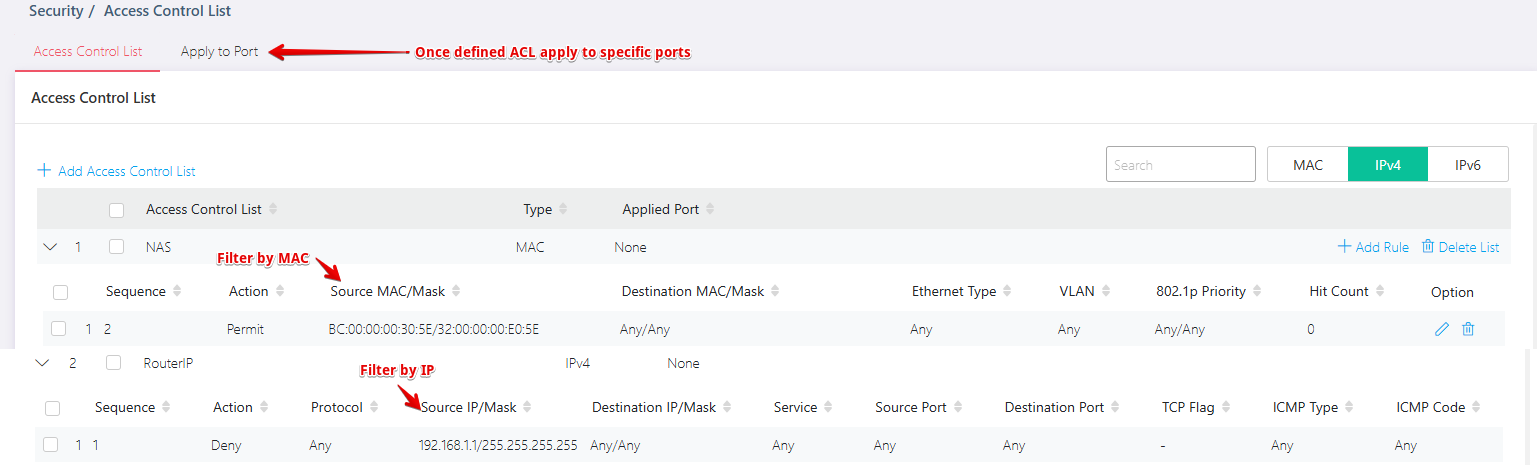
Use it to:
Block unauthorized MACs or IPs from accessing critical servers.
Shut down suspect connections instantly.
Apply rules globally or per port.
Example: MAC-based access rules silently block suspicious traffic—none of which would be caught by a traditional firewall.
Final Thoughts
Layer 2 security is no longer optional. The biggest threats aren’t always on the Internet—they’re already plugged into your network.
DrayTek’s advanced switch features offer SMBs a cost-effective and user-friendly way to implement true Layer 2 protection. Secure your LAN, stop internal threats at the source, and take control of your or your customer's network and run advanced like never before.
By adopting DrayTek’s Layer 2 security tools, businesses not only gain peace of mind but also position themselves to reduce costly downtime, protect valuable data, and build trust with clients who demand reliable infrastructure. MSPs and integrators can turn this into a clear value-add offering—enhancing their services and differentiating from competitors.

